In Task 19 of the TryHackMe Industrial Intrusion CTF, titled “No Salt, No Shame”, we dive into a cryptographic challenge that hinges on poor key management practices. The goal: decrypt sensitive files using a known passphrase, predictable AES parameters, and no salt or key derivation function. Let’s walk through how CyberChef becomes the MVP tool in solving this challenge.
Here is the original Task description
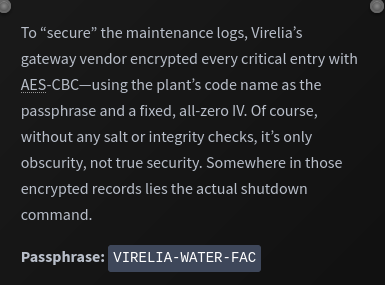
What we know:
- Passphrase known
- Algorithm known
- IV known
- No salt used (to derive key from the passphrase)
- Ciphertext / Encrypted files known
With that, you can just go to cyberchef and do:
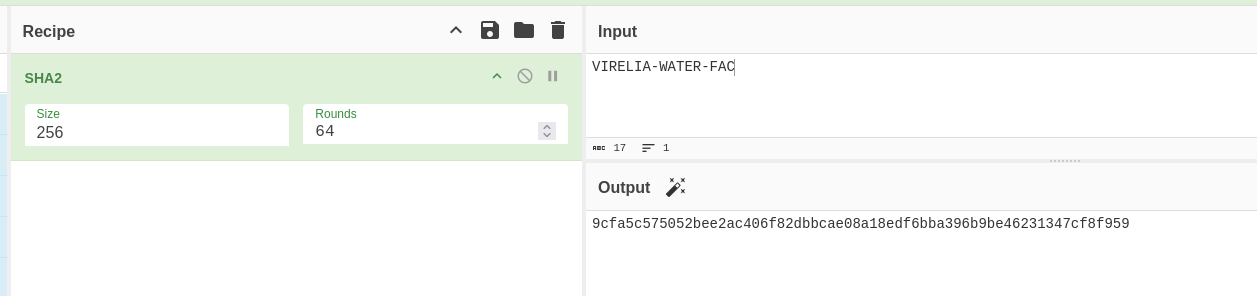
1: Load the SHA2 recipe, input the passphrase VIRELIA-WATER-FAC and hash it with sha256 (no salt used) like so, to get the AES key:
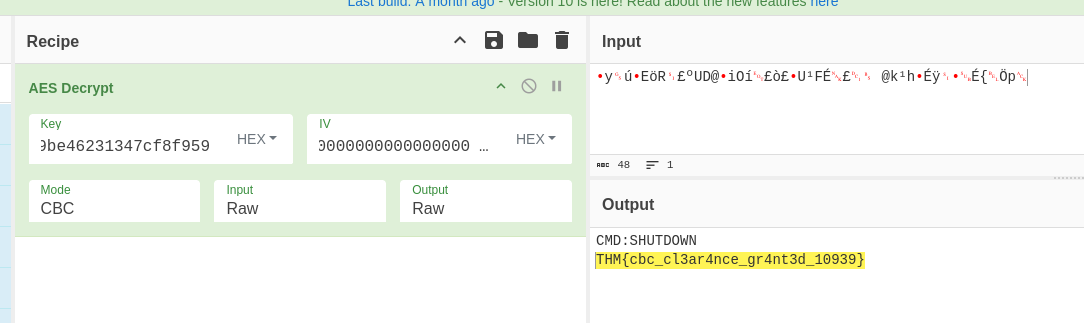
2: Open the encrypted file in cyberchef and add the “AES Decrypt” recipe. Input the key from the passphrase as hex value, set the IV to be all 0 and set mode to CBC (for AES-CBC). Win!
Note: Since keys are typically derived from a passphrase using a key derivation function, I had to manually determine the appropriate key size. The decryption could rely on any standard AES variant - AES-128, AES-192, or AES-256 - which require keys of 16, 24, or 32 bytes respectively. The passphrase VIRELIA-WATER-FAC is 17 bytes long in UTF-8, so it cannot be used directly as a valid AES key. Instead, I used a hashed version of the passphrase and experimented with different key lengths to match the encryption scheme.